Table of Contents
Home / Blog / Cryptocurrency
How to Strengthen the Security of Your White Label Cryptocurrency Exchange Software
August 19, 2025

August 19, 2025
Did you know that crypto investors lost a whopping 2.5 billion USD to scams and hacks in the first half of 2025?
That’s right! Hackers, scammers, and malicious actors recognize that the cryptocurrency industry is booming, and they are targeting every penny they can access.
Oh! That includes your “shiny” and “secure” white label crypto exchange software, built for convenience and security. Your provider might have told you it’s very secure, but sorry to break it to you: it isn’t immune to risk! Not at least if you don’t implement the robust security best practices we are about to share in this article.
If you’re ready to fend off attackers and keep both your company’s and users’ funds from malicious actors in the cryptocurrency space, this is your roadmap through this fight.
We’ll break down how securing crypto exchanges, especially white label crypto exchange deployments, requires more than standard precautions. You’ll see that it demands layered, proactive strategies. You’ll learn how to safeguard wallets and custody, fortify access points, ensure encryption integrity, lock down integrations, and select partners who prioritize security.
By the end, you’ll be equipped to lead with confidence, knowing that your white label crypto securities exchange platform is built on a trustworthy and resilient foundation.
But first, let’s get on the same page with some background knowledge.
Understanding the Basics of White Label Cryptocurrency Exchange Software Security
A white-label cryptocurrency exchange software is a customizable, pre-built, and fully functional crypto trading platform that enables businesses to launch their own cryptocurrency exchange without needing to build the core technical infrastructure from scratch.
This turnkey solution encompasses the core features of a crypto exchange, including a trading engine, wallet system, admin controls, APIs, and a customizable front-end interface. Once you acquire one, you just need to incorporate your brand elements, and you’re automatically open for business. In short, it is a turnkey model for quickly entering the cryptocurrency market.
However, while this model clearly saves time and development costs, it does not mean that a crypto exchange business doesn’t need to implement strong security practices.
Many crypto exchange businesses built with white-label solutions sometimes make this mistake, and the consequences can be quite devastating.
You see, while the white label provider secures core systems, such as the backend engine, wallet custody, and API frameworks, the client, on the other hand, must manage user authentication, access controls, compliance workflows, and the operational environment.
As a matter of fact, white label crypto exchanges built with white label crypto exchange software commonly face major threats such as the following:
- Hot wallet breaches targeting online funds
- API abuse through unprotected endpoints
- Credential stuffing using leaked login data
- Insider threats from staff with privileged access
- DDoS attacks to disrupt availability
- Compliance failures from weak KYC/AML procedures
Therefore, as a technical lead or decision-making executive at a crypto exchange business, you must know that while a white label crypto exchange platform may be turnkey, safeguarding it is an ongoing, shared commitment.
So, how do you go about securing a white label crypto securities exchange software?
In the next section, we highlight nine solid security best practices for you to follow.
Let’s examine them one after the other.
Related Read: Why White Label Crypto Exchange Is A Preferred Choice Of Startups?
Build a secure crypto exchange with expert guidance
Collaborate with crypto exchange experts to ensure your exchange meets all security best practices and communicates trust to the user
Core Strategies to Strengthen the Security of Your White Label Cryptocurrency Exchange Software
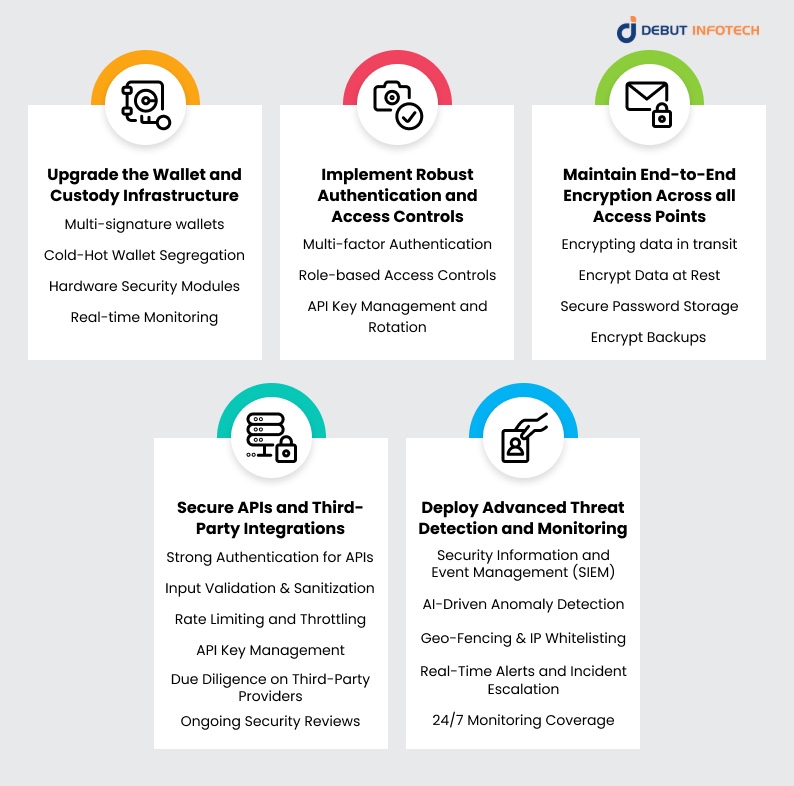
The following are some strategies you can use to build a layered defense for your white-label cryptocurrency exchange software:
1. Upgrade the Wallet and Custody Infrastructure
“Upgrading” the wallet and custody infrastructure of a cryptocurrency exchange means moving beyond default configurations and implementing cutting-edge measures to secure private keys, transactions, and storage environments. You must do this because the wallets contain the most valuable assets in your cryptocurrency exchange. As a result, they’re often the most attractive targets for attackers and malicious agents.
So, how can you upgrade the wallet and custody infrastructure?
The following are some significant upgrades that top decentralized exchanges use to upgrade their wallet and custody infrastructure:
- Multi-signature wallets: These are industry-grade wallets that require multiple approvals before authorizing any transaction. As such, before a user can withdraw funds, they will be required to provide approximately 2-3 authorized keys. By doing so, you eliminate a single point of failure, making it harder for attackers to access a user’s funds.
- Cold-Hot Wallet Segregation: As the name implies, this refers to maintaining a clear distinction between funds stored in hot wallets and those stored in cold wallets. More specifically, it involves using hot wallets for only operational liquidity while storing block funds in cold wallets. Finally, it also involves automating the daily transfer of funds from hot wallets to cold wallets, thereby minimizing the risk of losing a large amount of cryptocurrency funds.
- Hardware Security Modules (HSMs): HSMs are physical devices built for generating, storing, and managing cryptographic keys. These secure enclaves ensure that your sensitive private keys are never exposed in the raw form.
- Real-time Monitoring: You should monitor all activities in real-time by integrating systems that flag unusual withdrawal patterns, large fund movements, or transactions from unexpected geographic locations.
For executives and tech leads overseeing white label crypto exchange development, this is one of the first and most impactful security upgrades to prioritize. Your wallet system isn’t just a feature; it’s the vault of your entire operation.
2. Implement Robust Authentication and Access Controls
You can think of a secure wallet system as a safe vault, while authentication and access controls are the front doors or entry points to that vault. You see, no matter how secure a vault is, as long as an attacker can somehow gain legitimate entry or access to the front doors, all your security features wouldn’t matter. That’s why you must put measures in place to prevent unauthorized access to your white-label crypto exchange platform.
The following are some vital strategies to implement robust authentication and access controls on your crypto exchange platform:
- Multi-factor Authentication (MFA): MFA is an authentication protocol that requires both users and administrators to verify their identity using at least two factors. These factors are usually a combination of something they know (a password), something they have (a hardware token or OTP), or something they are (biometrics, such as fingerprints and facial recognition). This measure reduces the chances of success of any account takeover attempt.
- Role-based Access Controls (RBAC): Role-based access control systems assign permissions to different human agents within a system based on their respective job roles. For instance, an admin managing customer support would only have access to the customer support system and wouldn’t be able to initiate fund transfers. Similarly, developers shouldn’t be able to alter compliance settings. This significantly reduces the chances of unauthorized access via access point blind spots.
- API Key Management and Rotation: This ensures that API keys have limited scopes, are encrypted in storage, and are rotated regularly to prevent long-term misuse.
In white label crypto exchange development, authentication isn’t a “set-and-forget” feature—it’s an evolving line of defense that must adapt as threats change.
3. Maintain End-to-End Encryption Across all Access Points
Maintaining end-to-end encryption across all access points within a white label crypto exchange software means making sure that messages, transactions, and piece of sensitive data are securely locked in their intended locations, and only intended recipients can access them. Without doing this, anyone can intercept the messages moving between users, APIs, and servers, and you know what that means.
So, before you launch your white label crypto exchange software, implement end-to-end encryption by:
- Encrypting data in transit: You can encrypt all data in transit by securing all communication between browsers, mobile apps, APIs, and backend systems with the use of the latest protocols like TLS 1.3. This protocol prevents man-in-the-middle attacks and eavesdropping.
- Encrypt Data at Rest: Even when sensitive data is not in transit, it still needs to be stored with user information, wallet details, and trading records using strong encryption standards, such as AES-256. These encryption standards ensure that the data remains unreadable without the authorized keys, even if physical servers or backups are compromised.
- Secure Password Storage – Never store passwords in plain text. Instead, use modern hashing algorithms, such as bcrypt or Argon2, combined with unique salts, to render brute-force attacks impractical.
- Encrypt Backups – Your disaster recovery files are as sensitive as your production data. Ensure they’re encrypted and stored in secure, access-controlled locations.
It’s vital to put these measures in place because every access point, such as user logins, API endpoints, and internal admin panel, represents a potential entry for attackers. Full encryption ensures that even if attackers breach one layer, they can’t make sense of the captured data.
4. Secure APIs and Third-Party Integrations
APIs are the connective threads of any white-label crypto exchange platform, or of any technical architecture for that matter. They link trading engines, wallets, mobile apps, payment gateways, and even compliance services. They also connect third-party integrations to your core infrastructure. As such, a single vulnerable API or poorly vetted integration can compromise the entire exchange.
Therefore, you need to ensure that your APIs are uncompromised and that your third-party integrations are thoroughly vetted.
Here’s how:
- Strong Authentication for APIs: Verify all requests using OAuth 2.0 or signed JSON Web Tokens (JWT). This ensures only authorized apps and services can communicate with your systems.
- Input Validation and Sanitization – Don’t just let any data onto your crypto exchange platform. Instead, validate every incoming detail in order to screen injection attacks, malformed requests, and other input-based exploits.
- Rate Limiting and Throttling – Impose a limit on the number of requests that can be made per second from a given source to prevent brute-force or denial-of-service attempts through the API.
- API Key Management – Issue keys with the principle of least privilege. This means giving access only to the functions a partner truly needs. Take things up a notch by rotating these keys regularly and storing them in an encrypted format.
- Due Diligence on Third-Party Providers – Before integrating with payment processors, KYC/AML services, or analytics platforms, vet their security posture, regulatory compliance, and breach history.
- Ongoing Security Reviews – Schedule regular audits for APIs and integrations, including penetration testing to identify and fix weaknesses.
You need to implement all the best practices for decentralized crypto exchange development because they keep your APIs and third-party tools very flexible, which is a core strength of the platform’s security. By locking down these points of contact, you protect both your platform and your users’ assets.
5. Deploy Advanced Threat Detection and Monitoring
Most of the strategies we’ve explored so far have been focused on preventing attacks, and that’s a good thing. After all, prevention, they say, is better than a cure. However, in cryptocurrency exchange development, the chances of fully avoiding an attack are very slim, especially when you consider the increasing sophistication of cyber threats in today’s crypto world.
That’s why your white-label crypto exchange software must also be able to actively detect and respond to threats in real time. This is where advanced threat monitoring tools come into the picture. They give you eyes and ears across your entire infrastructure, alerting you the moment something suspicious happens.
Here’s how to strengthen your detection and monitoring capabilities:
- Security Information and Event Management (SIEM): SIEM systems help you identify unusual patterns and correlate different seemingly unrelated events by aggregating logs from your servers, applications, and network devices.
- AI-Driven Anomaly Detection: Leverage AI’s analytic capabilities by identifying and flagging unexpected trading patterns, login attempts from unusual locations, and unusual activities using machine learning systems.
- Geo-Fencing and IP Whitelisting: These security protocols ensure that only approved IP ranges can access admin panels or sensitive APIs. As such, they block logins from high-risk regions.
- Real-Time Alerts and Incident Escalation – Set up automated notifications to security teams when critical thresholds are met, such as large fund movements, multiple failed logins, or sudden spikes in API calls.
- 24/7 Monitoring Coverage – Threat actors don’t work on a 9-to-5 schedule. Ensure your detection systems are always active, with a team or service ready to act immediately.
The goal of these strategies is to identify unusual behavior promptly and halt it before it escalates into something devastating for your users and your platform.
Launch a high-performance crypto exchange platform with our customizable white label cryptocurrency exchange software
Contact our experts to customize our industry-grade white-label cryptocurrency software for growth in the cryptocurrency industry.
Conclusion: Choosing a Security-Conscious White Label Provider
Maintaining a secure cryptocurrency exchange platform isn’t a one-time task. Rather, it’s a continuous commitment. From upgrading wallet custody systems to securing APIs and monitoring for threats in real-time, each layer of defense builds trust with your users and keeps you ahead of evolving risks.
Yet, all those efforts might just be futile if you don’t begin with a secure white label cryptocurrency exchange software in the first place.
That’s why, when it comes to ensuring that your cryptocurrency exchange platform is fully secure, you must start by choosing white label crypto exchange development companies that prioritize security above all else. This means the white-label product offered by your provider should already have a layered security architecture with multi-factor authentication, cold storage, multi-signature wallets, and robust DDoS defenses.
These are just some of the security features we prioritize at Debut Infotech Pvt Ltd. Getting our white label crypto exchange software isn’t just about picking up a software over the counter; it’s more like partnering with a full-time collaborator that embeds security into every component.
Do you like the sound of that?
Get in touch with our crypto exchange developers to assess the security features you need today
Frequently Asked Questions (FAQs)
Q. What is a White Label Crypto Exchange?
A. A white-label cryptocurrency exchange software is a customizable, pre-built, and fully functional crypto trading platform that enables businesses to launch their own cryptocurrency exchange without needing to build the core technical infrastructure from scratch.
Q. Is a white-label crypto exchange less secure than a custom-built one?
A. Not always. The architecture of the supplier and your operating procedures determine security. However, with the right upgrades, audits, and monitoring, a trustworthy white-label crypto exchange program may equal or even surpass the security of many custom-built platforms.
Q. How often should I run security audits on my platform?
A. At the very least, perform quarterly vulnerability checks in addition to an annual comprehensive independent security audit. More regular penetration testing is recommended for high-volume platforms, especially after significant code upgrades, integrations, or regulatory changes.
Q. Can my provider handle all security, or do I need in-house staff?
A. Core infrastructure security is managed by a supplier, but daily monitoring, compliance, and access controls still require internal supervision. Both the operator and the vendor share responsibilities for security.
Q. Do I need compliance certifications before launching?
A. Achieving compliance—such as KYC/AML preparedness and relevant data protection standards—prior to launch enhances user trust, reduces legal risks, and often speeds up licensing procedures with regulators, even though requirements vary by jurisdiction.
Talk With Our Expert
USA
Debut Infotech Global Services LLC
2102 Linden LN, Palatine, IL 60067
+1-708-515-4004
info@debutinfotech.com
UK
Debut Infotech Pvt Ltd
7 Pound Close, Yarnton, Oxfordshire, OX51QG
+44-770-304-0079
info@debutinfotech.com
Canada
Debut Infotech Pvt Ltd
326 Parkvale Drive, Kitchener, ON N2R1Y7
+1-708-515-4004
info@debutinfotech.com
INDIA
Debut Infotech Pvt Ltd
Sector 101-A, Plot No: I-42, IT City Rd, JLPL Industrial Area, Mohali, PB 140306
9888402396
info@debutinfotech.com



Leave a Comment