Table of Contents
Home / Blog / Blockchain
How to Protect Your Web3 Project with Smart Contract Security Tips
October 23, 2025

October 23, 2025
Introduction
Blockchains were built on trustless technology, yet somehow, users still have to trust that a smart contract won’t break, leak funds, or behave unexpectedly.
And let’s be honest, nobody wants to wake up to another headline like “$200M lost due to overlooked vulnerability.”
This is precisely why smart contract security is not optional, it is what Web3 credibility is based upon. Be it a DeFi protocols, NFT marketplace, or enterprise automation system, users will not touch it until they realize it is safe, and you can prove it.
The good news? Ensuring the security of smart contracts does not need to seem intimidating and only suitable to high-ranking auditors. Risk could be reduced dramatically by anyone, with the correct process, tools, and mindset.
In this guide, we’ll break it down like you’re sitting with a trusted engineer over coffee:
- What actually makes a contract secure
- How to avoid the most common failure points
- And how to prove transparency without exposing sensitive logic
In Web3, security is not just protection, it is your competitive advantage.
What Is Smart Contract Security?
A smart contract can be likened to a vending machine at its core. You feed a system with an input, be it a payment or a digital action and the system autonomously performs the agreed outcome without human intervention.
Nevertheless, in contrast to a vending machine that could cost a few dollars in case of any malfunction, a defective smart contract could cost you a lot of money. Most smart contracts are not easily modifiable or fixable once they have been deployed to the blockchain. This renders security not only significant, but crucial.
Smart contract security is the set of practices, tools and programming methods that are applied to ensure that the code will act as intended, and cannot be modified by malicious agents. Secure smart contract languages, like Solidity with well-established safety patterns, or other languages like Vyper and Move with similar aims, are often used by developers.
Concisely, there is a chance that smart contracts eliminate the necessity of intermediaries, though it requires the code itself to be credible. Even a single vulnerability can break down an entire system when there is no good security measure in place.
Turn smart contract risks into your strongest asset.
Our security audits build trust and ensure your project’s foundation is unbreakable. Protect your vision and your users.
Common Smart Contract Vulnerabilities and Why They Matter More Than You Think
Even the smartest piece of blockchain code can be surprisingly fragile. One tiny mistake, an unchecked function or miscalculated number, and millions can disappear in seconds. That’s why smart contract audit services exist, not as a formality, but as protection against real, well-documented attacks.
To make things easier to digest, here’s a breakdown of the most common vulnerabilities you need to watch out for:
| Vulnerability | What It Means | Real Incident Example |
| Reentrancy Attacks | The contract keeps processing withdrawals again and again before the balance updates like someone convincing an ATM to spit money twice. | DAO Hack ($60M+) — the original smart contract disaster. |
| Integer Overflow / Underflow | When math gets messy. If a number exceeds allowed limits, it can flip into unintended values, letting attackers drain funds. | ERC-20 Token Exploits — multiple tokens were drained due to this simple math bug. |
| Oracle Manipulation | Contracts rely on external data (like price feeds). If that data gets tampered with, the entire system is tricked. | Price Feed Attacks — used to manipulate DeFi lending and liquidation systems. |
The scariest part? Most of these exploits were preventable.
They didn’t happen because blockchain technology was weak, they happened because someone skipped a second review, ignored a test scenario, or assumed “it’ll probably be fine.”
Security Best Practices for Developers
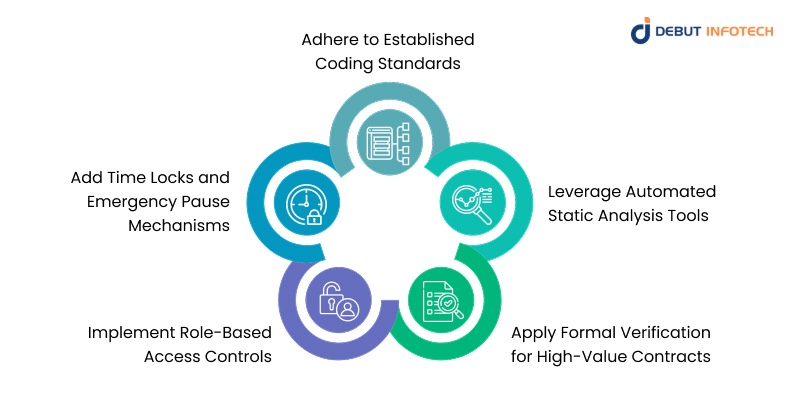
Smart contracts are only as solid as the precautions prior to deployment. In contrast to conventional software, it is not an option but a necessity to be secure since once a contract is live there is no simple rollback.
The following are the basic smart contract security best practices that any developer must consider in order to reduce risk and protect user trust.
1. Adhere to Established Coding Standards
Start with proven guidelines like the SWC Registry and OpenZeppelin standards. These frameworks help to deal with usual vulnerabilities and encourage uniform predictable conduct throughout contracts. Following them ensures you’re not solving problems that have already been solved by the broader blockchain community.
2. Leverage Automated Static Analysis Tools
Solutions such as Slither, MythX and Echidna are vital in identifying bugs and patterns that are exploitable early in the development cycle. They play the role of an automated safety net, detecting problems that could otherwise be missed in the process of manual reviews.
3. Apply Formal Verification for High-Value Contracts
In contracts involving substantial amounts of money or controlling protocol behavior, formal verification provides an additional degree of assurance. You decrease the chances of logic attacks by proving mathematically that the contract functions as intended.
4. Implement Role-Based Access Controls
Restrict key operations to specific addresses, including upgrades, withdrawals, and the issuance of tokens. The existence of clear access control frameworks prevents accidental mis-use and curbs internal threats.
5. Add Time Locks and Emergency Pause Mechanisms
Adding time-delays to critical operations will leave teams with time to respond in case something seems off. Similarly, kill switches (pause functions) enable operations to be suspended temporarily in the event of an alleged exploitation.
How to Ensure Transparency for Users & Businesses
When you’re dealing with smart contracts, security alone isn’t enough. People want visibility. Whether it’s retail users depositing funds or enterprise clients integrating your protocol, trust comes from openness, not just technical claims.
Here’s how leading projects are making their security practices transparent and verifiable:
1. Balance Open-Source Access with Professional Audits
The act of publishing your smart contract code publicly creates credibility, it indicates that you are confident enough to allow other people to inspect it. However, community review alone may be risky.
The best approach combines both:
- Private security audits first, to eliminate critical threats before launch.
- Open-source publication afterward, allowing external developers to validate your work.
This dual approach satisfies both security expectations and transparency demands.
2. Make Your Audit Reports Easy to Find and Easy to Read
Getting audited by firms like CertiK, Hacken, or Trail of Bits is a strong first step but the value is lost if the report gets buried in a PDF folder.
Users should be able to quickly answer:
- Was the audit recent?
- What issues were found?
- Did the team fix them or ignore them?
Plain language summaries of key findings (along with the complete report) imply accountability without overwhelming non-technical users.
3. Offer Ongoing Visibility with Live Monitoring Tools
Security shouldn’t end after deployment. Real-time monitoring through platforms like Tenderly or Dune Analytics helps detect unusual contract behavior immediately.
Even better, share the dashboard, or publish alerts when anomalies are flagged. This tells users: “We’re not just deploying and walking away, we’re actively protecting this system.”
4. Launch a Public Bug Bounty Program
Even the best audits miss edge cases. That’s why platforms like Immunefi, which has facilitated over $100M+ in bounty payouts, have become standard practice.
Offering rewards for responsible vulnerability disclosures is more than risk mitigation. It’s a proactive security signal that shows you’re not hiding behind your code, you’re inviting scrutiny.
Smart Contract Deployment Assurance Guidelines
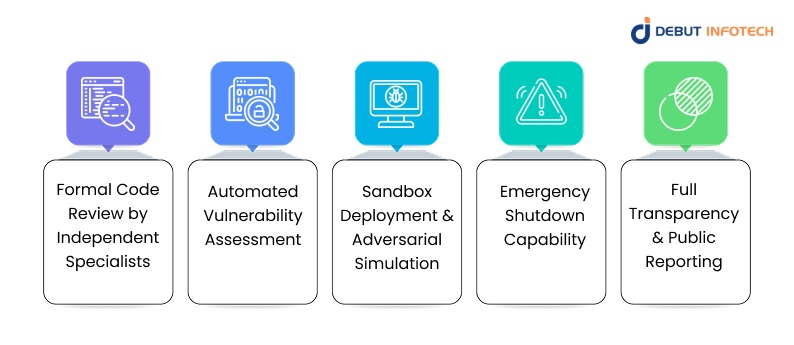
Deploying a smart contract without a structured review process is equivalent to launching financial software without compliance approval. To maintain both user trust and operational stability, every contract must satisfy the following audit criteria before going live.
1. Formal Code Review by Independent Specialists
A smart contract should be reviewed by external security professionals, not just the internal development team. This ensures:
- Objective validation of core business logic
- Assessment of privilege roles and admin powers
- Detection of hidden dependencies or upgrade weaknesses
Only proceed when all high and medium-severity findings are resolved.
2. Automated Vulnerability Assessment
Manual reviews must be complemented with automated tools to catch known exploit patterns. Recommended analyzers include:
| Tool | Detects |
| Slither | Reentrancy, incorrect inheritance, uninitialized storage |
| MythX | High-level attack vector modeling |
| Echidna | Logic-based fuzz testing |
These tools help cover recurring smart contract security issues that humans may overlook.
3. Sandbox Deployment & Adversarial Simulation
Before moving to mainnet:
- Deploy on a testnet or local fork
- Execute stress tests under extreme load
- Simulate malicious interactions and economic exploits
A contract that performs correctly only in ideal conditions is not production-ready.
4. Emergency Shutdown Capability
A well-designed contract includes contingency controls such as:
- pause() or stop() functions
- Multi-signature authority to trigger or revoke control
This allows stakeholders to react instantly in the event of a breach or market anomaly.
5. Full Transparency & Public Reporting
Users and partners must be able to verify that security processes were followed. Publish:
- Contract documentation with clear function visibility
- Audit summaries or full reports
- Statements outlining upgradeability and governance rules
Transparency is not just good practice, it’s a deterrent against speculation and doubt.
Smart Contract Security Case Studies
Theory can be helpful when speaking of blockchain security, though the real-world events demonstrate the reality of hazards and tasks the security team should undertake. Below are two well-known case studies that illustrate how proactive measures (or lack of them) can shape a project’s entire future.
- Uniswap V3
Uniswap V3 is frequently mentioned as an example of rigorous engineering in decentralized finance.
What Went Right:
The team used formal verification, in which core smart contract logic was thoroughly tested by deployment. This proactive role helped to avoid some of the critical weaknesses that would have caused significant financial damage.
What Fell Short:
Despite the strong security posture, users experienced gas inefficiencies, highlighting the trade-off between airtight security and operational performance.
Key Insight:
Security must go beyond “no exploits.” High-performing systems need protection and efficiency to guarantee durability and user confidence.
- Poly Network
Poly Network recorded one of the biggest hacks in blockchain history.
What Went Wrong:
One of the vulnerabilities in contract permissions allowed attackers to steal more than $610 million through the protocol.
What Happened Next:
In an unusual turn, the hacker returned the funds, claiming it was a “white-hat exercise.”
Key Insight:
Relying on ethical intent is not a strategy. Once trust is broken, damage to reputation lasts even after recovery. Ongoing reviews, outside assessments, and independent smart contract auditors are essential.
Ready for bulletproof smart contract security?
Our experts specialize in building and auditing vulnerability-free code tailored for your project’s safety and success.
Final Thoughts
Here’s the truth, once a smart contract goes live, there’s no “undo” button. That’s what makes blockchain powerful and risky at the same time. A single overlooked vulnerability can cost millions, damage brand trust, and stall innovation before it even begins.
That’s why we believe smart contract security isn’t just about audits, it’s about responsibility.
It means:
- Writing code like real money is on the line because it is.
- Testing beyond the happy path and preparing for the worst-case scenario.
- Being open, transparent, and accountable to your users.
And the good news? You don’t have to handle it alone.
At Debut Infotech, we work as your security partner, not just your blockchain development team. We help you design smarter, test deeper, and launch stronger so your users don’t just use your platforms, they trust it.
Because in Web3, trust isn’t claimed, we earn it.
Frequently Asked Questions (FAQs)
Q. What Is Smart Contract Security?
A. Smart contract security refers to the methods used to protect smart contracts on the blockchain from bugs, hacks, or misuse.
Once deployed, most smart contracts cannot be changed and many of them control real money. That means even a small vulnerability can lead to major financial losses.
To keep contracts safe, developers use practices like secure coding, thorough testing, professional audits, ongoing monitoring
These steps help prevent common risks such as reentrancy attacks, overflow errors, or uninitialized proxies. In short, smart contract security ensures the contract behaves exactly as intended without interference or failure.
Once deployed, most smart contracts cannot be changed and many of them control real money. That means even a small vulnerability can lead to major financial losses.
To keep contracts safe, developers use practices like secure coding, thorough testing, professional audits, ongoing monitoring
These steps help prevent common risks such as reentrancy attacks, overflow errors, or uninitialized proxies. In short, smart contract security ensures the contract behaves exactly as intended without interference or failure.
Q. How Much Does It Cost to Create a Smart Contract?
A. There’s no universal price tag for developing a smart contract. The final cost depends on several factors such as how complex the project is, which blockchain it’s built on, whether security audits are required, and if any third-party integrations or long-term maintenance are needed.
To give you a general range, a simple NFT minting contract might cost anywhere between $2,000 and $10,000. However, more advanced systems like DeFi platformsor DAO infrastructures can easily go beyond $150,000.
If you’re unsure where your project falls on that spectrum, the best approach is to request a custom estimate based on your specific requirements.
To give you a general range, a simple NFT minting contract might cost anywhere between $2,000 and $10,000. However, more advanced systems like DeFi platformsor DAO infrastructures can easily go beyond $150,000.
If you’re unsure where your project falls on that spectrum, the best approach is to request a custom estimate based on your specific requirements.
Q. Can Smart Contracts Be Updated After Deployment?
A. Yes, but only if they’re intentionally designed to be upgradeable. By default, smart contracts are immutable, which means once they’re deployed, the code cannot be changed. This is great for security, but it also means you can’t fix bugs or improve functionality unless you plan for it in advance.
To enable updates, developers often use what’s called a proxy pattern. In this setup, the contract separates its storage (data) from its logic (code). When an upgrade is needed, a new version of the logic can be deployed while keeping the same contract address and stored data intact. That way, the contract behaves differently without losing its history or requiring users to migrate.
To enable updates, developers often use what’s called a proxy pattern. In this setup, the contract separates its storage (data) from its logic (code). When an upgrade is needed, a new version of the logic can be deployed while keeping the same contract address and stored data intact. That way, the contract behaves differently without losing its history or requiring users to migrate.
Talk With Our Expert
Our Latest Insights
USA
Debut Infotech Global Services LLC
2102 Linden LN, Palatine, IL 60067
+1-708-515-4004
info@debutinfotech.com
UK
Debut Infotech Pvt Ltd
7 Pound Close, Yarnton, Oxfordshire, OX51QG
+44-770-304-0079
info@debutinfotech.com
Canada
Debut Infotech Pvt Ltd
326 Parkvale Drive, Kitchener, ON N2R1Y7
+1-708-515-4004
info@debutinfotech.com
INDIA
Debut Infotech Pvt Ltd
Sector 101-A, Plot No: I-42, IT City Rd, JLPL Industrial Area, Mohali, PB 140306
9888402396
info@debutinfotech.com



Leave a Comment